
Preview in:
Have you ever wondered if the image of your face is safe online? There are many ways to check if you've shown up in any database. Online face lookup goes beyond a simple search. If you're curious about the technology behind face recognition, how features are compared, and how to keep your images safe in case of leaks, keep on reading!
Unlocking Phones vs. Finding Faces Online
Facial recognition isn't one-size-fits-all. You're likely familiar with Face ID, maybe even using it daily. But the technology behind it works differently from simply recognizing a face in a photo.
The table below breaks down the key differences between tools used to unlock your phone or laptop and those used to search for faces online.
Access control
Examples: Face ID, Windows Hello
Principle of work: TrueDepth camera that projects a structured light pattern onto your face. The camera captures the distortion of this pattern, creating a 3D depth map of your facial features.
Data extraction: Key facial features like your eyes, nose, mouth, and the space between them are identified and converted into a mathematical representation.
Matching process: The mathematical representation (facial data) is stored in a secure enclave within your device's processor. During unlocking, the newly captured 3D scan is converted into a similar mathematical format and compared with the stored data. A successful match grants access.
Search from image
Examples: lenso.ai, PimEyes
Principle of work: Extracting features from an image uploaded by the user. The user-uploaded image undergoes preprocessing to enhance clarity, reduce noise, and potentially normalize for lighting variations.
Data extraction: Key facial features like your eyes, nose, mouth, and the space between them are identified and converted into a mathematical representation.
Matching process: A matching algorithm scores the similarity between the user's facial data and entries in the index. Images with scores exceeding a certain threshold are presented as potential matches.
Digging deeper - how are images stored and compared?
All reverse image search tools use Content-Based Image Retrieval (CBIR). This system lets you search for images using other images instead of text descriptions.
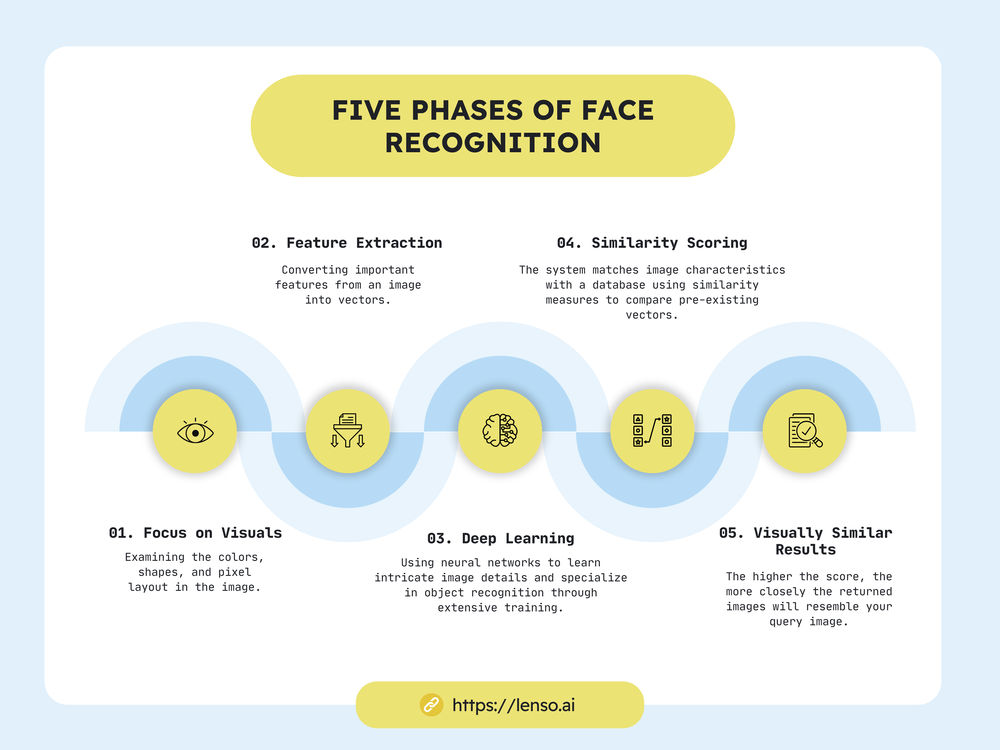
Focus on Visuals: It analyzes colors, shapes, and pixel arrangement, not text descriptions.
Feature Extraction: CBIR extracts key features from your image and converts them into a digital format (vectors).
Deep Learning: Uses layered neural networks to progressively learn complex features from images. With enough training, these networks can become experts at recognizing specific objects.
Similarity Scoring: The system compares your image features to an index using similarity measures (comparing vectors that were created before).
Visually Similar Results: The higher the score, the more visually similar the returned images will be to your query image.
Comparing facial features
Now, you may be wondering how the system finds facial features and how it compares them. The software used in facial recognition tools creates a map of a person's face. This map is a representation of geometric shapes and distances between one's facial elements, such as eyes, nose, and mouth.
Map is then converted into a vector, and this vector is compared with the images in the index. The closer the scores are to each other, the more likely the faces are a match.
If you want to edit some of your images, you should try face editor.
How to perform a search? Find your own face online.*
Here’s how you can find your face online using lenso.ai:
- Visit lenso’s website: https://lenso.ai/.
- On the main page, upload a picture of your face. Make sure it’s clear and all features are visible.
- Select the area of your face if needed, or simply search with the entire image.
- Make sure to choose the “People” category.
- Click on the image that matches your search to be redirected to the website where it appeared. This way you can find out where the image was posted and take steps to get it deleted.
Tip: Sign up for lenso’s automatic email notifications: Whenever lenso.ai finds a match for your face, you'll receive a prompt notification via email.
*Available only in selected regions
What is facial recognition used for?
Security and Access Control:
- Unlocking devices: Smartphones and laptops can use facial recognition for secure logins, often combined with session hijacking prevention protocols to stop attackers from stealing access tokens.
- Securing buildings and sensitive areas: Facial recognition systems can grant access based on pre-approved individuals.
- Law enforcement: Facial recognition can help search for suspects or missing persons in videos or public camera footage.
Daily Convenience:
- Social media: Platforms like Facebook can automatically tag people in photos using facial recognition.
- Payments: Some stores and payment systems allow facial recognition for secure transactions.
- Smart homes: Facial recognition can personalize smart home settings or control access to specific features.
Other Uses:
- Marketing: Stores might use facial recognition to tailor advertising based on demographics.
- Event management: Facial recognition can streamline entry at events or verify ticket holders.
- Finding missing people: Law enforcement can use facial recognition to scan public footage for missing individuals.
Security concerns and law changes toward face recognition tools
Research published in 2016 raised privacy concerns, suggesting that facial recognition systems accessible to law enforcement might encompass more than 133 million Americans, representing more than half of American adults. \
Due to the report published by Georgetown Law, efforts to regulate facial recognition gained momentum. In Maryland, a legislator proposed a bill to establish guidelines for its use.
Meanwhile, the ACLU in Vermont advocated for a complete ban on applying the technology to driver's license photos. On a broader scale, the National Institute of Standards and Technology enhanced its testing procedures by including regular assessments for bias based on demographics.
Finally, the U.S. House Oversight Committee convened a hearing to examine the FBI's implementation of facial recognition.
The 2016 study sparked a nationwide debate about police use of facial recognition. While the laws are still being changed and the technology keeps evolving, this report made people think about how to use it fairly. As things move forward, it's important to keep talking about how to balance safety with privacy.
Want to find out more about reverse image search? Read more here: The Principles of Reverse Image Search. How it Works & What You Can Do
Leaked Photos: Here's How to Fight Back
Feeling violated because private images of you surfaced online? You're not alone, and there are steps you can take to regain control.
- Take Charge of Your Accounts - lock it down: Change passwords on all potentially compromised accounts. Double up your security with two-step authentication.
- Gather Evidence:
- Screenshot it: Capture the leaked images and any surrounding details.
- Search it: Use a reliable image search tool to see if the photos spread further. Be aware, these tools have limitations, so a more thorough search might be needed.
- Report the Abuse:
- Silence the source: Most platforms allow reporting of non-consensual intimate content. Use their reporting tools.
- Get legal help: Leaking private photos can be a crime. Consider contacting the police, especially if the photos were obtained without your consent.
- Seek Support:
- Talk it out: Confide in a trusted friend or family member.
- You're not alone: Crisis hotlines specialize in online harassment. Reach out for support.
- You can contact the Cybersmile Foundation: https://www.cybersmile.org/
Facial search demystified
In this article, we tried to encapsulate all the most important information regarding facial recognition and looking up one’s face online. While the facial recognition tool is used widely, and it’s an amazing, helpful technology, it is also important to secure your image and privacy. This is why new laws were enforced, regulating the issue.
Nowadays, there are multiple foundations set up to help in case of images being leaked. Make sure to check what you can do when this happens to you.
Continue reading

General
Searching and Comparing Photos Online: The Power of Modern Technology
The internet has made it easier than ever to find and share photographs – but in the past, searching for an image could be a frustrating experience. You might have had to look for a needle in a haystack using keywords or scroll through page after page of results to see if your query had been correctly interpreted.

General
Top 6 Reverse Image Search Websites for Face Recognition in 2026
If you find yourself struggling to find the perfect reverse image search engine that supports face recognition, you’re in the right place. Here are our top 6 picks.

General
Visual Intelligence: Using AI Reverse Image Search to Drive Sales and Market Share
The era of exclusively text-based searching has ended. People now upload screenshots, crop product photos, and snap pictures of storefronts. The image has become their search query.

General
List of All Tools for Finding Similar Images in 2026 (Search by Image)
Looking for similar images online? Here’s the list of all the similar image search websites - fast, reliable and accurate image search engines. Check which tools you can use for searching for photos on the internet.
